Well, at first, you really should consider start using Azure Active Directory ;-). However, there are other options. In this article, I will talk about:
- Options for connecting SaaS applications
- Customers without Azure Active Directory
- External identities
- B2B collaboration
- Azure AD B2C
Connecting should be made easy
As a service provider, you should let your customers know how to connect. I often see it that a service provider develops an application and only offers a single solution to connect. And they don't provide any details about how the connection can be made. They don't offer any guidance whatsoever on the details of the connection that you need to set up. Consider making a step-by-step guide for the customers who will use your product. Not everybody has the knowledge to set up a federation trust without a metadata URL and guess all the specific settings.
Connecting should be made easy because identity, federation, single sign-on, and the protocols that come with it aren’t that easy at all. After years of experience, I still need to get my head around some parts, and therefore it's a good practice to do some research and write things down, like in an article such as this :-).
Add more options for a broader platform
As a service provider, you decide which connection options you want to make available in your application. Do you only allow connections through SAML? OpenID Connect (OAuth 2.0) through multi-tenancy? Both? Maybe add some more flavors? You decide. By adding more options, you have a broader platform for your customers to connect, so the design in the image below is one to keep in mind.
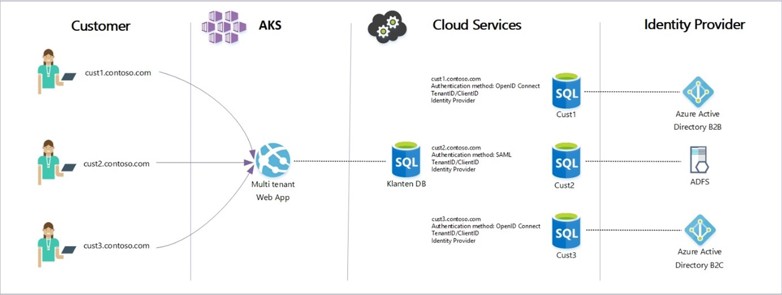
In this design, every customer is using a unique DNS entry that points to a multi-tenant web app hosted within, for example, AKS. The web app uses a customer database that keeps track of the connection settings each customer is using.
Customers without Azure Active Directory
There are lots of customers that are not using Azure Active Directory. As a service provider, if you are using Azure Active Directory, you want to use Azure technology as much as possible. As mentioned in the first article using a multi-tenant application, users in any Azure AD tenant will be able to sign in to your application after consenting to use their account with your application. The OpenID Connect (OIDC) protocol is used for this (OIDC is a simple identity layer on top of OAuth 2.0).
Next to that, SAML authentication is commonly used with identity providers such as Active Directory Federation Services (AD FS) federated to Azure AD, so it's often used in enterprise applications. SAML is still the most common protocol being used, but nowadays, Microsoft prefers OIDC.
Azure offers multiple options for making SAML connections, set-up single sign-on or federation. But which one is the right one for you? Suppose you are developing an application and want your customers to connect through SAML and provide them with a metadata URL. In that case, you need to look at External Identities in Azure Active Directory.
External Identities in Azure: two scenarios
With External Identities in Azure AD, you can allow people outside your organization to access your applications and resources while letting them sign in using the identity they choose. Your customers, partners, distributors, suppliers, vendors, and other guest users can bring their own identities. This can be any identity like a company identity or an unmanaged social identity like Google or Facebook, they can use their own credentials to sign in. The external user’s identity provider manages their identity, and you manage access to your applications with Azure AD to keep your resources protected. Within External Identities, you have two scenarios:
- B2B collaboration; where you share applications and resources with external users
- Azure AD B2C; offers a white-labeled identity management solution for consumer and customer-facing applications
B2B collaboration
Azure Active Directory business-to-business (B2B) collaboration is a feature within External Identities that lets you invite guest users to collaborate with your organization. With B2B collaboration, you can securely share your applications with guest users from any other organization while maintaining control over your corporate data. A simple invitation and redemption process lets partners use their credentials to access your company’s resources. This is primarily used for collaboration between companies and often not when acting as a service provider.
Within the Azure Portal, you can configure a B2B collaboration through SAML by going to Azure Active Directory > External Identities > All identity providers > New SAML/WS-Fed IdP. The metadata URL the guest can use looks something like this: https://nexus.microsoftonline-p.com/federationmetadata/saml20/federationmetadata.xml.
Azure AD B2C
Azure Active Directory B2C provides business-to-customer identity as a service. It also takes care of the scaling and safety of the authentication platform, monitoring, and automatically handling threats like denial-of-service, password spray, or brute force attacks.
Azure AD B2C is a separate service from Azure Active Directory (Azure AD). It is built on the same technology as Azure AD but for a different purpose. It allows businesses to build customer-facing applications, allowing anyone to sign up for those applications with no restrictions on the user account.
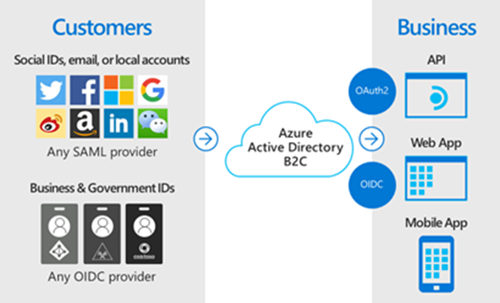
Azure AD B2C is a white-labeled authentication solution. You can customize the entire user experience with your brand to blend seamlessly with your web and mobile applications. Customize every page displayed by Azure AD B2C when your users sign up, sign in, and modify their profile information.
Within Azure AD B2C, you need a custom policy to make federation with an STS like ADFS possible. The metadata URL the customer can use looks something like this: https://your-tenant-name.b2clogin.com/your-tenant-name.onmicrosoft.com/your-policy/samlp/metadata?idptp=your-technical-profile
Final note: always an easy SaaS connection
Whether your customers are using Azure AD or not, letting them connect to your SaaS application should be possible and made easy. You can provide different solutions for different customers, and External Identities is there to help! There are multiple possibilities, and I am ready to help you sort them out if you want. You can contact me at fsuper@intercept.cloud.
In the third and last article of this series, I will show you the details of an ADFS instance connected to an Azure AD B2C application. Did you miss the first article in the series? Read it here: 'How to connect your SaaS application.'