- In the first article, we discussed how important automation was to shifting left. Similar to the last article, on Azure DevOps, the tools we explore here will help you automate detection and, in some cases, remediation of vulnerabilities in your codebase.
- Some of the tooling mentioned previously are applicable to both Azure DevOps and GitHub. With that in mind, let us explore some GitHub-specific functionality that you might find useful. Many of the tools mentioned below are already built into the GitHub offerings and do not necessarily require 3rd party involvement.
- It is important to note that some of this functionality is specific to certain licensing levels. Public repositories, such as Open-Source projects, can also benefit from additional features when compared with private repositories.
For more details on the pricing structure vs. feature set, please visit the pricing of Github.
Secret Scanning in GitHub
It might sound like one of the easiest things to get right but inadvertently committing secrets (usernames and passwords, API tokens, or other credentials) is a very common error when developing software. This is especially true if your teams are under pressure to deliver against a deadline.
This is where the automated secret scanning can be invaluable. This built-in feature (with Advanced Security licensing) relies on patterns provided by partners and organizations like yours. When secret scanning is enabled, GitHub scans commits to a repo for secrets and generates alerts if any are found.
You might think that scanning commits after the commit has been made is akin to closing the barn door after the horse has bolted. You’d be right, by that point you may have already exposed your credentials or tokens. You can also enable “Push Protection” to ensure that any commits that contain secrets are blocked.
You can access all these settings within the “Code Security and Analysis” settings for your repository. Just look for the “GitHub Advanced Security” section.
Code Scanning options in GitHub
Another built-in feature for those companies with the Advanced Security licensing, Code Scanning analyses your code repositories for coding issues and vulnerabilities.
By default, code scanning uses GitHub’s own CodeQL engine, but you can use any third-party tool that supports SARIF data. Check out the docs for more information.
Code scanning is another valuable resource in your toolbox when you’re trying to develop secure software. You can configure CodeQL to scan and triage your code on a schedule or it could be triggered by a Pull Request. As with secret scanning, this generates alerts for your developers to work through.
You can then make use of Branch Protection rules to ensure that Pull Requests can’t be merged if your code scanning fails. See below for the setting you need from within your Branch Protection rules:
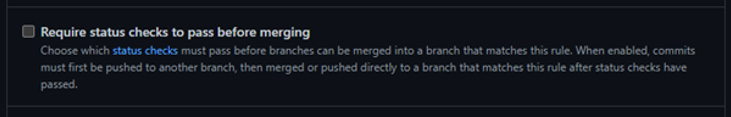
From the above section, just select the exact checks you need to succeed before a merge can be completed.
Dependabot makes you aware of insecure dependencies
Think of Dependabot as your friendly, reliable, neighborhood Robot that keeps a close eye on your code repositories.
Dependabot can help you with making sure that you are aware of any insecure dependencies. You can enable Dependabot by default for all new repositories from your personal account or organization settings. See the code security and analysis image below for details.
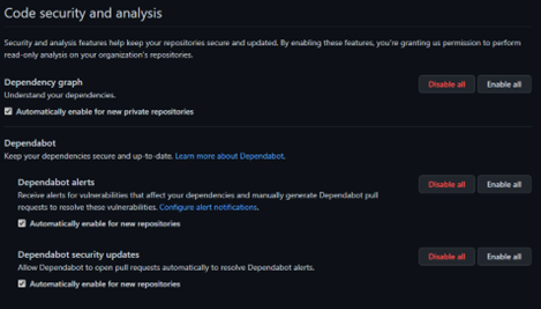
You can go even further with Dependabot by configuring security updates, where it creates Pull Requests automatically when it detects a vulnerable dependency. This allows you to act swiftly we package you rely on to create your application is found to have a vulnerability.
You can even give Dependabot more responsibility by taking advantage of the version updates feature. This feature is similar to the security updates feature mentioned above but, with version updates, it creates pull requests whenever dependencies have new versions available, regardless of whether it is vulnerable or not.
Get started with GitHub Docs
As with most of the tools and services mentioned over the course of these articles, it’s important to get practical experience with them. It’s important to learn how they work and what benefits or constraints they may provide to your business.
You can get started with the tools mentioned above by heading over to the GitHub Docs. Also, you will find guides and learning paths here as well.
Git Guardian: a possible alternative
For those that don’t like to put all of their eggs in one basket, there is a 3rd party option called Git Guardian that integrates with your GitHub organization. I have only started to look at the possibilities with Git Guardian so your mileage may vary. I wanted to mention it here in the interests of balance. You can find out some more about Git Guardian.
The importance of tooling and automation
I have mentioned it a few times throughout this short series on “Shifting Left”, but it bears repeating. The tools, extensions, and services mentioned in this series are only a snapshot of what is available in the ecosystem. As you continue shifting to the left, the tooling you use become integral to your success. As your journey progresses, you will settle on what group of tools and services work for your organization. They won’t always be the same as the next team or company.
As a team of developers or DevOps engineers, it’s impossible to detect and remediate all vulnerabilities and technical debt alone. This is where your chosen tooling becomes very important. Choosing tooling that automates the detection and, where possible, remediation will make it easier for your team to focus time on your backlog instead of chasing vulnerabilities. Choosing the right tooling will ultimately return benefits in agility, efficiency, and time to market.
Closing thoughts
The purpose of this series of articles was to highlight the importance of “shifting left” as a software creator or development team. We explore the what, why, and how of shifting left as well as practical tips for progressing that journey in Azure DevOps and GitHub.
One important thing to take away from this series is that, as your software development processes, security and shifting left is an iterative process. This journey will be one of many cycles, where you’re improving your processes, tooling, and automation with each iteration.
Intercept assists customers with their journey to the cloud every day. Feel free to reach out for advice and/or sparring sessions with our expert team.

