The evolution of Azure Firewall
At Intercept, we enable ISVs to build their applications using the power of Microsoft Azure. Over the last while, we have seen more and more customers implement Azure Firewall to help protect their Azure resources.
Many customers use the Web Application Firewall, with App Gateway or Front Door, to protect the front-end of their application from inbound attacks. Whether for audit and compliance reasons or a desire to improve their overall security posture, we also see an increase in the use of firewalls to protect outbound traffic flows from those same applications.
Incorporating Azure Firewall into your platform architecture might look like the below example diagram.
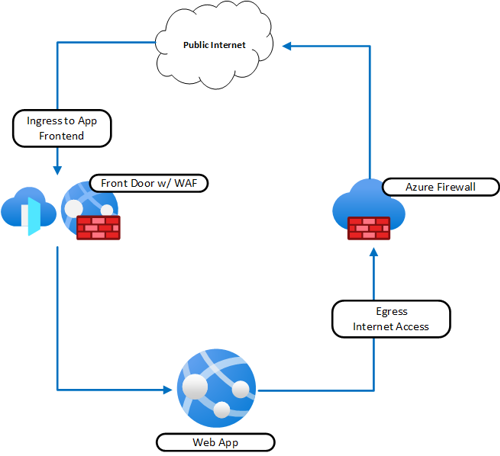
Using Azure Firewall allows you to protect your virtual network by controlling what traffic is allowed into and out of your network. Azure Firewall has a “deny by default” configuration which means that all traffic that doesn’t match a specific rule is denied. This rule allows for fine-grain control over the firewall ruleset, and ultimately the security of your application.
What is Azure Firewall?
Azure Firewall is a managed network security service that protects your Azure Virtual Network and the resources contained within it. It is fully stateful and has built-in high availability and scalability.
Azure Firewall allows you to create and enforce application and network rulesets to suit the needs of your environment. It’s also fully integrated with Azure Monitor, which allows for log collection and analysis.
The Azure Firewall also uses the Microsoft Threat Intelligence feed to protect your network from known malicious sites.
What is Azure Firewall Premium?
Azure Firewall Premium is the evolution of Azure Firewall towards a feature set we would expect from traditional Next-Generation Firewall (NGFW) or Unified Threat Management (UTM) appliances.
Having been made generally available on July 19th, 2021, you can now take advantage of some new features with the Premium SKU. At a high level, these new features are as follows:
- TLS Inspection: You can use Azure Firewall Premium to inspect outbound and east-west TLS traffic. Encrypted traffic is decrypted by the firewall and processed against the configured rules before re-encryption and delivery to its destination.
- IDPS (Intrusion Detection and Prevention System): With this new feature, you can monitor and block traffic for unusual and malicious behavior. The new IDPS feature is signature-based and works to detect malware as well as Command and Control activity.
- URL Filtering: With Azure Firewall Standard we were able to configure rules based on FQDNs. With the new Premium tier, we can now work with a full URL. This tier allows for greater granularity in the rules we can create.
- Web Categories/Web Filtering: Anyone who has configured NGFW/UTM devices will be familiar with the new web filtering functionality. Using Azure Firewall Premium, you can now block entire categories of web traffic from leaving your Azure networks. For example, you can stop gambling or social media access using these new rules.
How does Azure Firewall Premium compare?
There are some features that I’d like to see added to the Azure Firewall service. Such as controlling which IP address the firewall uses for specific outbound traffic flows or the ability to integrate it with Azure AD or AD to allow the configuration of user-specific rules.
That being said, the Premium tier is another excellent step by the Azure Firewall team to bring more parity between the native Azure Firewall and the 3rd party offerings available from WatchGuard, Sophos, Palo Alto, Check Point, and the like.
Why would I use Azure Firewall?
With the introduction of these new premium features, Azure Firewall becomes a compelling option for protecting your Azure networks. Add to that the fact that it’s natively integrated with the existing logging and monitoring you’re already using in Azure Monitor and the fact that you don’t need to worry about scalability or availability, as the platform takes care of that for you.
I’d need a good reason not to lead with Azure Firewall in my designs moving forward. Yes, there are still some missing features I would like, but they aren’t enough to make me opt for a 3rd party firewall solution.
What would I use it for?
I hear you saying: “That’s great and all but, I work in use cases. Tell me where I can use it”.
Let me help you with that…
If you’re deploying anything in an Azure Virtual Network, you should be considering how you’re going to secure the resources that reside on your network. Usually, this means implementing a firewall, whether it’s a Web Application Firewall, Azure Firewall, or perhaps both, as seen in the example above.
With the new premium features detailed above, the use case that jumps out to me most is using Azure Firewall Premium to protect your Azure Virtual Desktop deployment. The TLS Inspection and Web Filtering features would be particularly relevant in ensuring that you protect your AVD users and your Azure network from malicious sites and malware.
As mentioned at the top of the article, another use case we see more and more of is using Azure Firewall to protect egress traffic from an application stack. In one of our most recent deployments, we use Azure Firewall and NAT Gateway to protect and control egress traffic from multiple AKS clusters in a hub/spoke virtual network deployment.
Concluding...
Azure Firewall is an excellent choice to secure your Azure resources. I expect that the team behind Azure Firewall will continue to add features to both standard and premium tiers. As mentioned above, I will be leading with Azure Firewall when designing solutions for our customers.