As we explore together, we will mention specific tools. It should be noted that there are often multiple tools that will accomplish the same or similar goal. It is up to you, as a business, to evaluate the options and decide which is the best fit.
The tools we explore here will help you automate detection and, in some cases, remediation of vulnerabilities in your codebase. We will dive into the following tools and topics:
- Gitleaks
- SonarQube
- Whitesource Bolt
- Container security
- The importance of tooling
- The conclusion
- DevOps with Intercept
Gitleaks
Gitleaks is a SAST (Static Application Security Testing) project that scans your git repos for hardcoded secrets. These secrets can range from credentials (usernames/passwords) to API keys and tokens. Find out more about the Gitleaks project.
You can install Gitleaks locally and use pre-commit hooks to ensure that you don’t commit secrets to your git repositories in the first place.
You can also incorporate Gitleaks into your Azure DevOps Pipelines using the Gitleaks extension. Using a YAML-based pipeline, you might start with the following snippet to scan your source repository.
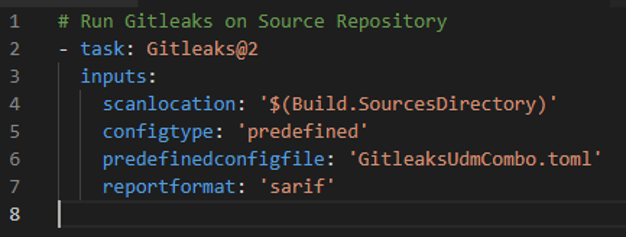
If you find already committed secrets in your repository, it is essential to completely remove them from your repository, both git history and the codebase itself. At this point, you should consider any committed secrets as compromised and change them immediately. GitHub has good documentation on removing sensitive data.
SonarQube
SonarQube is a tool that continuously inspects your codebase with the aim of protecting your project or application from poor code quality, security vulnerabilities, and technical debt. Capable of analyzing multiple languages, including C#, C++, Java, Python, and more.
Using the SonarQube Azure DevOps extension, you can introduce “Quality Gates” to your pipelines. This can allow you to fail a build or pipeline if you have a failed analysis. This serves to protect you from moving to production with problems in your codebase.
One extremely useful feature is the ability to block the merge of a Pull Request if there is a failed Quality Gate. You can find further information on how to configure this within the SonarQube Docs pages.
WhiteSource Bolt
If you’re creating open-source software or working with open-source dependencies, you might have heard of WhiteSource Bolt. WhiteSource Bolt is a free Azure DevOps extension that detects open-source components within your codebase. It then scans for known vulnerabilities and license issues.
According to their documentation, the extension enables you to:
- Detect and remediate vulnerable open-source components;
- Generate a comprehensive open-source inventory report per build;
- Enforce open-source license compliance, including dependencies.
You can incorporate WhiteSource Bolt into your Azure DevOps pipelines. Please see the documentation linked above for usage details; however, you can start with the below snippet to use WhiteSource Bolt in your pipeline definitions.

WhiteSource also provides a “full solution” that supports more languages and tools, among other feature additions.
Suggested read: Migrate TFS to Azure DevOps Services
Container Security
Container Security from Aqua Security is an Azure DevOps extension. If you’re using Azure DevOps pipelines to build your container images, then you might find this extension useful.
The extension allows you to add a step to your container image build process. This step would check images for issues and vulnerabilities before they get pushed to your container registry of choice.
The importance of tooling
The above tools and extensions are only a snapshot of what is available in the ecosystem. As you continue shifting to the left, the tooling you use becomes integral to your success. As a team of developers or DevOps engineers, it’s impossible to detect and remediate all vulnerabilities and technical debt alone. This is where your chosen tooling becomes very important. Choosing tooling that automates the detection and, where possible, remediation will make it easier for your team to focus time on your backlog instead of chasing vulnerabilities. Choosing the proper tooling will ultimately return agility, efficiency, and time to market benefits.
In conclusion…
The purpose of this article was to highlight some of the tools/extensions available within the Azure DevOps ecosystem which might help you on your journey as you shift left. As mentioned above, these aren’t the only tools available and are only mentioned to give an idea of what is possible by exploring the extension ecosystem.
In the following article, we will talk about practical ways that you can “shift left” using tooling, extensions, and automation within GitHub.


