In this article we discuss:
Let's get in!
What is Cloud Native security?
Cloud Native security is an approach to building and deploying secure applications in the cloud, with security in mind for both the application and infrastructure from the start.
In this model, we integrate security into the entire software lifecycle, from coding to testing to deployment to runtime. It’s about securing the application, the continuous integration (CI) and continuous delivery (CD) infrastructure, and all software artefacts such as container images, dependencies, and Software Bills of Materials (SBOM).
In Cloud Native environments, security is part of everything you protect – from operating systems to containers to applications. It follows the application wherever it goes, whether that’s in the cloud, on containers or in a host system.
What is the goal of Cloud Native security?
The goal of Cloud Native security is to protect against threats and vulnerabilities specific to cloud environments by using solutions. By having security at every stage of the software lifecycle, applications in the cloud can be continuously protected and resilient.
Suggested read: What is Cloud Security?
Traditional Security vs Cloud Native: How it differs
The security approach for these applications differs from traditional on-premises solutions because Cloud Native environments are more dynamic and scalable and have a shared responsibility model between the cloud provider and the customer.
Cloud Native security is built in from the inside out, monitoring applications continuously and protecting them at runtime.
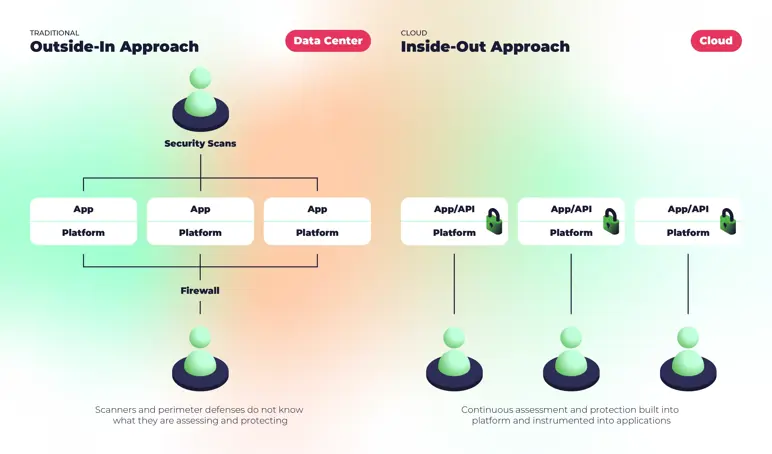
Traditional security is built for static environments with fixed IPs, isolated systems (hardware or hypervisor) and persistent workloads. In contrast, Cloud Native environments are dynamic, and workloads are constantly spun up and down.
Rather than fixing issues in production, we must now integrate security earlier in the development process (shift-left). This is due to frequent automated releases in the CI and CD pipeline.
Traditional methods included proprietary code and little open-source. However, this new model requires software composition analysis, vulnerability scanning, and SBOM. SBOM gives visibility into the components of a software supply chain and is crucial for reducing supply chain security risks.
Network security, which used to be based on static hardware configurations, must now adapt to a dynamic environment. To secure the network, permanent addresses are replaced by changing addresses at the subnet level, where identity needs to be verified across security groups, resource groups and labels. This way, traffic can be controlled while pods are being orchestrated.
With the rise of multi-clouds, organisations must focus on their cloud provider’s security configurations, not the infrastructure itself. This changes how we think about security in a Cloud Native world.
The 4 C’s of Cloud Native security
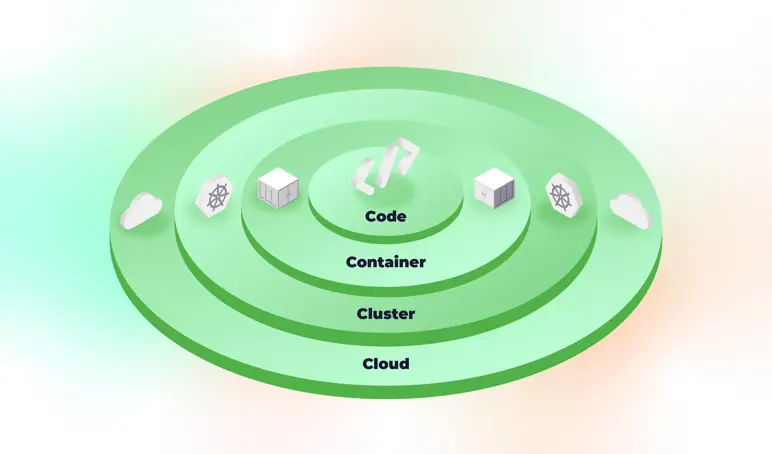
When it comes to Cloud Native security, there are four primary layers to consider for container security:
- Cloud
- Cluster
- Container (Pod)
- Code
The order matters because each layer of the security model builds on the next outermost layer. We could also refer to this as "defence in depth". It’s a series of defensive mechanisms layered to protect valuable data and information.
Imagine: a malicious actor is attempting to access your data. So, what security layers will they need to penetrate?
1) The first layer is the cloud layer (Microsoft Azure).
2) Then we have the cluster layer (Kubernetes).
3) The third layer is containers, managed through Kubernetes, which package your application and its runtime for consistent operation.
4) Finally, you have your code, which may also include your data or information.
Without further ado, we’ll discuss them in detail:








