The necessity
A little bit of background. Security traditionally focuses on protecting access using solutions as Conditional Access, Azure Bastion, and Zero Trust architecture. Or focuses on secure service publishing of services with e.g. Azure Front Door and a Web Application Firewall.
A notable trend is the increasing number of data breaches. It increased to 422 million last year, which is a 300% spike in relation to the previous year. Further, the enhanced risk profile and sensitivity of the compromised data, paired with an upsurge in zero-day exploits, intensifies the threat of unauthorized users in your Azure environment.
After the wave of Cryptolocker attacks in the last years, we are now seeing a massive increase in illicit crypto mining or crypto-jacking attacks. This attack uses the massive scale of Azure to deploy large numbers of high-powered Virtual Machines with GPUs to mine for Cryptocurrency on compromised Azure environments. The attacker uses a compromised account to gain access and automatically deploys VM Scale sets to as many regions as possible.
The costs of these Cryptomining environments can easily reach over €100K a day and if the actor targets a tenant or subscription that’s not used or monitored, this all can remain undetected for weeks Believe us, you want to avoid scenarios like the above 😉
To help you avoid those, we share 5 practices that will help you minimizing the chances of the above scenarios:
1. Cancel unused Azure Subscriptions:
It's paramount to protect your organization against the misuse of your cloud environment. We recommend canceling unused subscriptions as they can be targeted by malicious actors. Azure Subscriptions that are not managed by a (CSP) partner could be risky as potentially nobody is monitoring the consumption, but it does contain a billing account for direct (unlimited) invoicing.
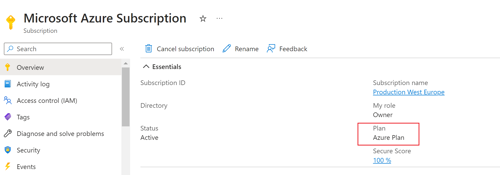
You can check your subscription(s). Log on to the Azure Portal and check your available Subscriptions. Partner offered Subscriptions use “Azure Plan”, direct bill subscriptions can be called for example “Pay-As-You-Go“.
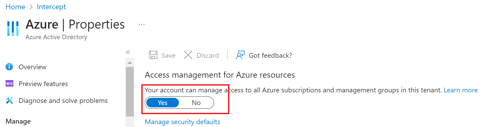
Ensure you are able to see all Subscriptions in your tenant(s) by using the Global Admin account and enabling the “Access management for Azure resources” option in the Azure AD Properties blade:
Microsoft has in recent years offered sponsorship Subscriptions, often with free credits for the first year, so it's important to check this using an Owner account.
2. Disable unused Azure Regions using an Azure Policy:
The region policy bicep file shows how to you can define a policy to restrict deployments to only the specified regions. Please note that you will have to assign this policy at the subscription, management group, or resource group level for it to take effect. If you have any questions implementing this technical change, feel free to contact us.
This particular Bicep code defines a policy that only allows resources to be deployed in regions specified in the allowedRegions array. It then assigns this policy.
3. Disable N Class VMs:
The Bicep file ‘disallowcreationsofNseries’ creates a policy rule for checking for virtual machines that have an SKU name starting with 'Standard_N' which represents the 'N' series of VMs. If such a resource is found, the policy's effect is to deny the creation of that resource. The policy is then assigned to the current scope (which is the scope from where this Bicep file will be deployed).
If you have any questions how to disable deployment of expensive GPU powered VM's, feel free to contact us.
4. Set Azure Costs Alerts and enable anomaly detection:
Using Azure Cost Management you can enable two kinds of cost alerts:
- Anomaly detection: the aim of this feature is to help you detect unusual cost spikes and anomalies in your Azure spending. It utilizes AI, machine learning, and statistical algorithms to analyze the historical cost patterns and then identify any cost anomalies, i.e., spending that deviates significantly from your usual cost trend. This can help you proactively monitor your Azure costs, and quickly identify and investigate unusual spending.
- Cost Alerts: setup budget alerts to notify you when your spending for a particular scope (like a subscription or resource group) exceeds a certain defined threshold

5. Protect your workload by enabling Microsoft Defender for Cloud:
Microsoft Defender for Cloud serves as an integrated, cloud-based platform for application security. Its purpose is to fortify your defense against cyber threats, offer protection against contemporary dangers, and mitigate risk throughout the cloud application lifecycle in both multi-cloud and hybrid infrastructures. Intercept recommends enabling Cloud workload protection plans.




