Understanding Keys, Certificates, Secrets
To understand how Azure Key Vault works, we must discuss what it aims to do. Azure Key Vault lets us store and retrieve 3 types of sensitive information:
- Keys: A secure place to store cryptographic keys used for encryption and decryption.
- Certificates: Used for cryptographic authentication, such as accessing third-party services.
- Secrets: These include passwords, connection strings, and similar credentials.
Keys Explained
When we talk about keys, we refer to those used in cryptography, such as:
- Private Key: Known only to the issuer (the person or application that creates or uses it) and used for decryption and signing.
- Public-Private Key Pair: A pair of keys that can securely identify users and applications, allowing them to authenticate and access resources. The public key is shared openly, while the private key is kept secret.
- Public Key Infrastructure: A framework that uses cryptographic keys for secure communication and authentication.
A key is crucial to cryptographic communication, specifically within Public Key Infrastructure (PKI).
How it works?
A key is a file or a string of text that encrypts and decrypts data. Think of it as a literal and figurative key that unlocks encrypted information, making it accessible (unencrypted) only to those with the correct key. This can include API keys or service keys for securely interacting with applications.
Certificates Explained
Unlike keys, certificates are primarily about proving identity and enabling secure communication. They act as digital IDs, verifying identity and ensuring secure interactions between applications, services, and users.
Certificates are complex cryptographic objects used for:
- Authentication: Authenticate an application or user to another system.
- Encryption and Decryption: Encrypt and decrypt data based on identity.
- Secure Communication: Ensure secure communication by signing the communication, ensuring it has not been tampered with and originates from a trusted source.
Secrets Explained
Secrets are passwords, or any long string of information stored as text. They can include API keys, encryption keys, connection strings, and even certificates formatted as text.
Secrets function as credentials, allowing systems to authenticate or encrypt communications. They are commonly used to store sensitive data or enable encrypted communication between network devices.
Storage Containers in Azure Key Vault
We can find two types of Azure Key Vault that can be deployed:
- Standard Key Vault
- Managed HSM Pools (Hardware Security Module Pools)
Standard Key Vault
A Standard Key Vault is a multi-tenant managed service in Microsoft Azure. This means that while your Key Vault is dedicated to you, it coexists with other tenants on Microsoft's infrastructure. When choosing vaults as a container type, your data will be stored on a computer or hard disk. It provides basic security features but incurs some additional fees.
Managed HSM Pools
Alternatively, you can opt for Managed HSM modules as a container type. Microsoft maintains a pool of Hardware Security Modules to store information (secrets, keys, certificates).
HSM, short for Hardware Security Module, is a hardware device managed by Azure where information is stored. Rather than storing them on a computer, they are stored in a special device designed to protect these kinds of information. They are more secure than software-based storage, since keys never leave the hardware module. This makes them ideal for environments with high-security demands.
Note the following:
- Within Standard Key Vault, you can store both normal keys and HSM-backed keys.
- Within Managed HSM Pools, you can only store HSM-backed keys (software-based keys cannot be stored there).
Authentication in Azure Key Vault
To use Azure Key Vault, you first need to authenticate to it. This is done by connecting the application via Microsoft Entra ID (formerly Azure Active Directory).
Communication Flow:
- The communication flow is bi-directional, with requests passing from the application to Key Vault.
- Authentication is managed through Entra ID.
The visual below illustrates the authentication process further:
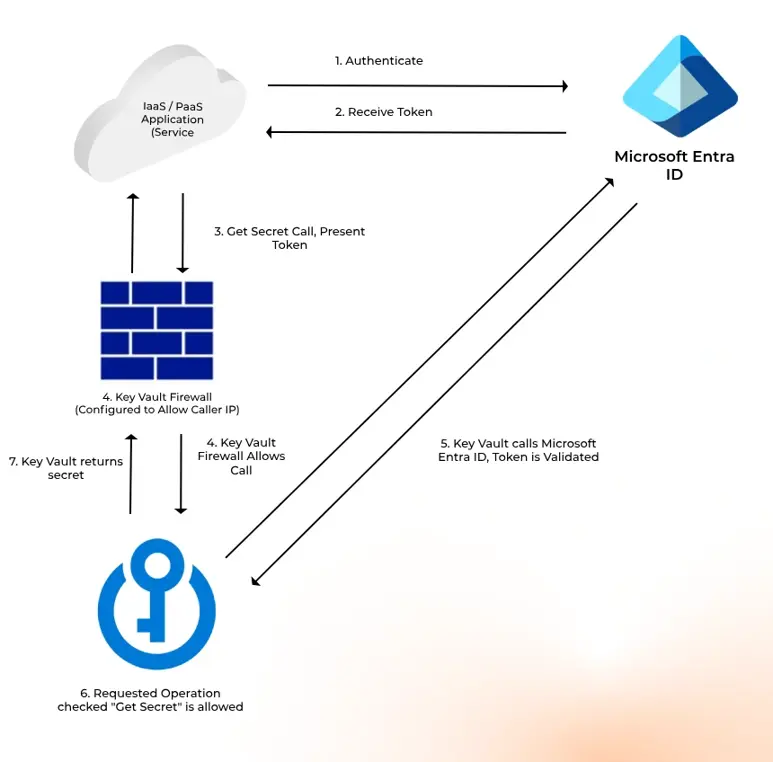
By setting this up, the application can securely identify itself, retrieve the necessary resources, and interact with users when delivering services.
Authorisation in Azure Key Vault
On the other hand, authorisation can be managed through either:
- Azure role-based access control (RBAC)
- Key Vault access policies
The first is Key Vault access policies. In simple terms, Key Vault controls who or what (applications, IPs, or entities) can access specific resources with specific permissions.
Access policies are limited to controlling access to the data only within Azure Key Vault. In other words, you cannot control access to Key Vault itself. In case you want to allow someone to manage the Key Vault, you cannot do that with access policies. For that, you need to use Azure Role-based access control (RBAC).
With Azure RBAC, you can control:
- Access to the data within Key Vault
- Manage access to Key Vault itself
When a user or application requests access to a key, Key Vault does not decide directly. Instead, it delegates the request to Microsoft Entra ID, which checks Role-Based Access Control (RBAC) to determine whether the user has the necessary permissions to access the requested resource.
RBAC acts as both a control and data layer, managing access to the data within Key Vault and controlling access to Key Vault itself.
Because access policies are now seen as legacy, we recommend using RBAC.
Safety and recovery features in Azure Key Vault
Deleting an encrypted storage account is about as bad as it gets. Without key, your data encryption key is locked up too – which means data is lost.
That’s why there are two key settings you must be aware of:
- Soft Delete
- Purge Protection
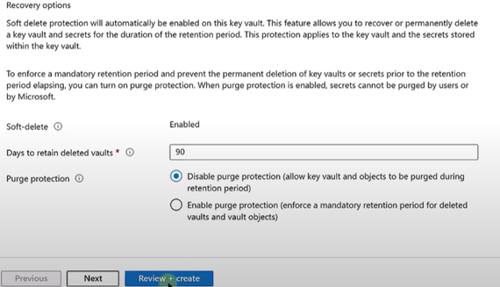
Soft Delete
When soft delete is turned on, you can restore items even if you accidentally delete them. If you delete a Key Vault, or any keys, secrets, or certificates inside it, they remain in a soft deleted state for a configured retention period (up to 90 days, with a minimum of 7 days). This prevents accidental deletions of important data.
If you created a Key Vault in the past, soft delete may not have been enabled. However, all newly created Key Vaults will always have soft delete turned on.
But if exploited, soft delete alone may not be enough: an item could still be purged before recovery is possible. Therefore, you also need to consider purge protection.
Purge Protection
Purge protection adds an extra layer of security on top of soft delete. It prevents items from being permanently deleted before the retention period expires.
For example, if the retention period is 90 days:
- Without Purge Protection: you can manually purge a soft-deleted key at any time within 90 days.
- With Purge Protection enabled: you must wait until the full 90-day retention period is over before it can be permanently deleted.
By default, purge protection is disabled. But when you enable purge protection, it cannot be bypassed. This ensures that even if an attacker or user tries to purge a deleted key, they will not be able to do so until the retention period expires.