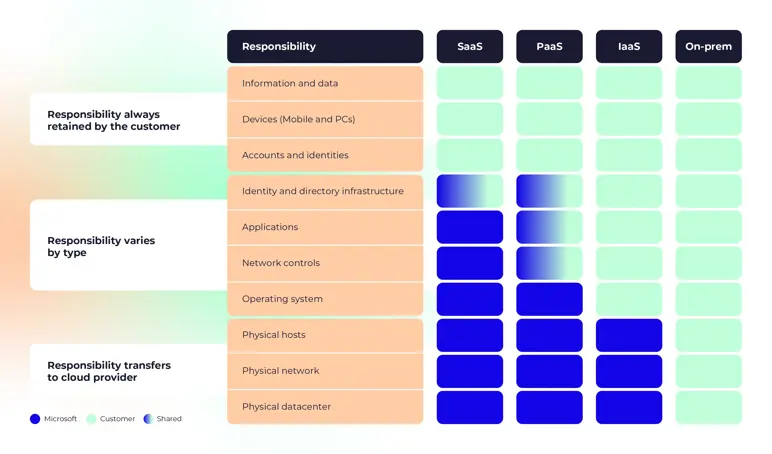
| Platform as a Service (PaaS) |
|
Compute Layer:
- Firewalls, IP address filters
- Service endpoints to prevent outside Azure access
- Private endpoints for stricter security
|
|
Data Layer:
- Network access lists for storage accounts
- IP address ranges for allowed access
- Virtual Networks and VPN
- SAS tokens (limited time/use, optional IP filtering) for public content
|
|
Management layer:
- Apply Conditional Access (MFA, IP restrictions) to management portals for stronger administrative security.
|
Even though a blob or file may be publicly accessible, SAS tokens give additional granularity for access control. This is a lower-impact measure compared to enforcing Private Link across everything, but it still significantly improves security.
3. Broken authorisation: Giving every Azure user the Owner role
Another common pitfall in Azure is broken authorisation—granting overly broad access within the management plane, where every Azure user is an owner. This happens in any organisation, project, or size, whether big or small, even within the scope of subscription or some of these very broad scopes.
When onboarding new users, it’s common to copy the first user’s access—turning role-based access control (RBAC) into a “everyone has full rights” scenario.
The problem is that the Owner can manage user access, create, update, and delete assignments, and invite anyone in. Additionally, they can create, read, update, and delete any resources within their scope. At the subscription level, a single Owner can remove other users, delete newly created resources, or grant access to anyone with an email address.
Mismanaged access like this creates major security risks across your Azure environment.
Best Practices
This is what you should do instead:
- Separate administrative duties in Azure across roles. The Contributor role can handle most resource management tasks, while the User Access Administrator role should manage role assignments. Splitting these responsibilities ensures no single person has unrestricted control over both resources and access, thus improving security.
- Assign roles at the resource group level rather than the subscription level. Remember that static RBAC assignments remain until removed, so evaluate them regularly when making changes.
By managing roles carefully, splitting duties, and applying governance, you reduce the risk of accidental or malicious misuse of privileges in Azure. Use Management Groups and Azure policies to setup this up.