What is IaaS security?
Infrastructure-as-a-Service (IaaS) security refers to the protective measures, protocols and technologies to protect the cloud infrastructure. IaaS is a cloud computing service where cloud providers offers key computation, storage, and networking resources on demand, yet in a virtual environment. There are many Infrastructure-as-a-Service (IaaS) providers, such as Microsoft Azure, AWS, etc.
With IaaS, organisations “rent” infrastructure components, such as Virtual Machines (VMs), storage and networking from IaaS providers. Thus, you no longer have to purchase, own and manage physical servers and data centres. This makes it a much more flexible and scalable option for organisations.
IaaS: shared responsibility model
A common misperception of companies is thinking that adopting IaaS, such as in a “lift and shift”, frees you from all security responsibilities. Instead, the opposite is true. Even though you become cloud-based, you are still responsible for cloud security. Regardless of which cloud computing model you choose, there is always a shared responsibility in the cloud – between the user and the cloud service provider.
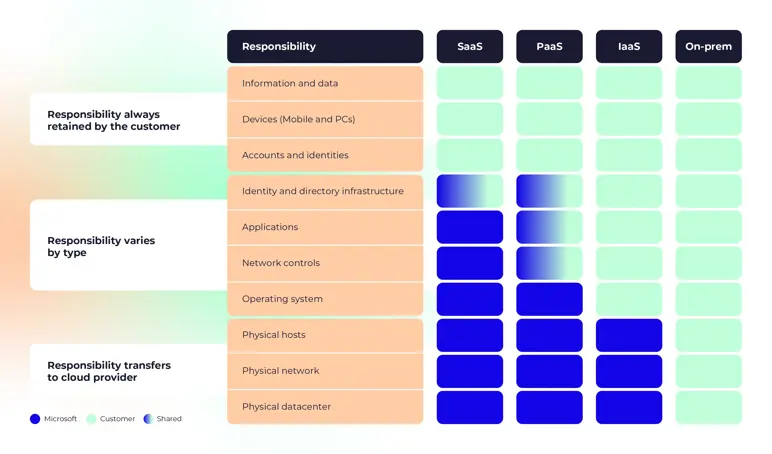
The IaaS model includes the maximum level of responsibility for the user. In an IaaS model, the cloud provider is responsible for managing the infrastructure. Think about maintaining the hardware, network connectivity (to the internet), and physical security. In addition, the IaaS provider is also responsible for security on the hypervisor layer.
On the other hand, as a user (system administrator), you’re responsible for all that’s left:
- Managing and installing the operating system (OS)
- (Network) configuration
- Middleware
- Runtime (OS’s libraries and additional tools required for the program to function)
- Database and storage configuration
As an infrastructure-as-a-service (IaaS) user, you install your chosen operating system and any necessary software on your rented virtual server. This creates the runtime environment where your applications can run, so you are responsible for managing this.
As opposed to the other models, such as PaaS or SaaS, IaaS gives you the maximum control over your cloud resources. Thus, many often argue it’s the most flexible category of cloud services. But it also means you have the highest level of responsibility, which includes securing your cloud infrastructure as well.
What are the benefits of IaaS Security?
IaaS environments are more scalable than maintaining on-premise data centres. You can spin up or down based on demand without the hassle of having to purchase or maintain hardware. Besides, there are fewer capital expenses with IaaS as an organisation does not need to purchase or maintain hardware. This frees budget, to be allocated to business goals.
10 IaaS Security Risks and Vulnerabilities
While it gives much more flexibility, scalability and convenience than managing your own data centres, IaaS also introduces a range of risks and vulnerabilities since you must trust your data, compute resources, and networking to an external service provider.
Virtualised computing resources, which are a core offering of IaaS, are particularly susceptible to security threats, making it crucial to implement effective management and security measures to protect them.
The risks involved with IaaS include:
1. Misconfigurations
Misconfigurations are the number one cause of vulnerabilities in IaaS. One wrong setting can cause big problems. These happen when resources like firewalls, access controls or storage buckets are not set up correctly and your infrastructure is exposed. For example, a misconfigured VM with open ports or weak credentials can be an easy target for attackers. Regular configuration checks and audits help mitigate these risks. Misconfigurations can be particularly challenging in multi cloud environments. This is why effective cloud orchestration is crucial for automating the management and coordination of resources across various cloud services.
2. Unauthorised access
In the cloud, authorised users can access resources from any device connected to the internet in a few clicks. Weak authentication, misconfigured access controls or stolen credentials can let unauthorised users get to your resources. Attackers can exploit identity management vulnerabilities such as brute force or phishing to compromise user accounts. Unauthorised access can lead to data breaches, intellectual property theft or disruption of critical operations.
3. Data leaks
Within IaaS, your data storage is internet-connected with cloud resources only a click away for users. This makes it a target for hackers looking to steal information. Moreover, the vast amount of data hosted by cloud providers is often a big temptation for malicious attackers. Data leaks happen when sensitive information is exposed to unauthorised individuals or systems. In IaaS setups, this can happen through misconfigured storage accounts, unsecured APIs or excessive permissions.
4. Permanent data loss
Data loss in IaaS can occur due to accidental deletions, ransomware attacks, hardware failures, or natural disasters. For example, attackers might penetrate your system and delete critical data. This can be either as part of a ransomware attack or to cause operational disruptions.
5. External threats
- Malware: Threat actors might deploy malicious software onto the cloud-based systems.
- Denial of Service (DoS) or Distributed Denial of Service (DDoS): An attack on availability where threat actors use an individual endpoint or many different machines to overwhelm the capacities of a cloud-based system.
- Man in the Middle Attacks: These occur when a threat actor tries to intercept information when it's being transmitted.
6. Insider threats
Insider attacks can happen when an ex-employee looks for revenge and still has access to resources, causing trouble.
7. Shadow services
Shadow services are cloud instances deployed by users without the IT department’s awareness or approval. Consequently, they might not have adequate security measures, which can cause more vulnerabilities and increase the risk of data loss or disclosure.
8. Compliance
Compliance falls under the responsibility of both the user and the cloud service provider. Failing to meet industry regulations can result in fines and damage to reputation.
9. Limited control and visibility
The IaaS model means cloud providers take care of the infrastructure. Thus, users are left with less control than being on-prem. Components such as networking equipment and storage devices are out of hand reach, which can cause concerns about the implementation of security measures.
10. Compromised Identities
Compromised identities and authentication pose significant security risks in IaaS environments. Threat actors can obtain credentials to cloud accounts through various means, such as installing keyloggers on admin computers or conducting phishing attacks. Once they gain unauthorised access, they can exploit the cloud provider’s API or user interface to manipulate services and grant themselves further access.